If you think that you can avoid malware by simply staying away from suspicious websites, we have bad news for you. You can also get malware from visiting legitimate websites. In this article, we’re talking about malvertising (short for malicious advertising).
Let’s take an in-depth look at the malvertising definition, including what you can do to decrease the risk of becoming a victim.
What is malvertising in cybersecurity?
Malvertising is a sneaky form of malware that exploits ads on trusted websites. However, before you get upset with The New York Times or Yahoo about malware-infected ads, we need to emphasize that these outlets have no idea that their ads have been compromised.
The hackers and cybercriminals behind malvertising place malicious code in these legitimate forms of advertising, relying on a victim’s trust in that site. When someone clicks on one of these ads, they are diverted to another site, one with nasty surprises waiting.
How malvertising works, and where it appears online
Now, you’re likely wondering how malicious code gets into these ads in the first place. The answer is that cybercriminals make the ads themselves, featuring innocent-looking products, and submit them to the sites they want to target.
Here’s a breakdown of how malvertising works:
- The criminals make professional, flashy-looking ads for innocuous products like designer handbags or tech products.
- They then insert malicious code inside those ads.
- The attackers submit those ads to ad networks and pay for their placement. The ads lead to websites in their client roster. Obviously, the ad network has absolutely no idea what they’ve been given.
- When the ads appear on websites, people will click on them, be sent to a completely different website, and be subject to a malware attack.
So, what types of sites are usually targeted? Criminals are obviously strategic in where they place the ads:
- High-traffic websites: Sites with low traffic would be pointless to target. Cyber criminals want as many victims as possible in a short time, before the code is discovered and removed.
- Search engines: Sponsored ads on search engines are not always as they appear to be. Again, these are high-traffic sites with plenty of opportunities.
- Social media: How often do you look at Facebook and Instagram only to see your feed clogged with ads? Not all of them are malvertising, but a few might be.
- Mobile apps: If you play a lot of iOS games, for example, you’re familiar with the experience of the game stopping to divert you to in-game ads. These could be malvertising scams, too.
How malvertising differs from adware
So far, malvertising attacks may sound a lot like adware. But there are some differences between them.
As we’ve said, malvertising is malware embedded inside a legitimate-looking ad, submitted to ad networks, and then sent on to high-traffic websites.
On the other hand, adware is a slightly different beast. Adware is often buried in free software downloads. Once the victim downloads the free software, they get the malware as well.
The risks of a malvertising attack
Like all forms of malware, a malvertising attack can be devastating to victims:
- The malware inside the ad can be something vicious, like spyware, keyloggers, trojans, remote access trojans, other adware, browser hijackers, or ransomware.
- Malware only brings more malware. The first will send you to the second, which is usually something much worse.
- The malware that gets into your device will go to town and start stealing sensitive personal data and browsing habits. This data will either be used by the hackers themselves or will be sold to third parties on the dark web.
- Your device will start to suffer performance-wise. Sluggish speeds, an overheating battery, crashes in your browser or operating system… the list goes on.
- Your browser settings will likely be changed. This includes your homepage, your search engine, and security settings.
- In most cases, the damage caused to the computer and the network, as well as the financial fallout from losing sensitive data, means that victims will have to pay to get the damage repaired.
- If businesses inadvertently send malware to clients and suppliers, their reputation will take a serious hit, which could even lead to a business closing.
So, how can you spot malvertising?
Let’s now look at how you can spot malvertising so you can take prompt action to shut it down. You should bear in mind that a lot of these signs also apply to other forms of malware.
Your monitor starts showing lots of pop-up ads
Since malvertising is defined as malicious ads, the first sign is lots of intrusive ads suddenly appearing on your screen. These ads are often high-urgency warnings, urging you to click right away.
You end up on the wrong website
You clicked on an ad for expensive shoes, and you ended up on a site with adult content. That is something that will likely not escape your attention. Being redirected to a completely different site is a major red flag.
Your browser starts acting strangely
Your browser is your gateway to the internet, so it makes sense that criminals will target it. That’s how they grab your browsing data, such as your IP address, search queries, login details, and more.
If your homepage changes, your default search engine is now something else, or your browser security settings have been disabled, then you have an unwelcome visitor on your hands, pulling the strings in the background.
Your machine starts moving slower than a snail
MacBooks are usually zippy devices, so if yours starts to seriously slow down and eventually crash, you may have something on your laptop that shouldn’t be there.
Malware is a real system hog, so your CPU will shoot through the roof. This, in turn, will overheat your battery, which will crash the browser and, eventually, the MacBook itself.
Your antivirus platform will send you warnings
Of course, the definitive proof of malvertising — or any other form of malware — is your antivirus platform sending you warnings. It goes without saying that you shouldn’t ignore these security alerts.
What to do if you clicked on malvertising and suspect malware
Since malvertising relies on trusted websites hosting their malware ads, it’s not entirely your fault if one ends up on your device. It’s now time to focus on how to get that nasty critter off there.
Disconnect from the internet immediately
Malware relies on a connection to its own server. By severing the connection, you’re already crippling it. So, turn off the Wi-Fi right away and keep it off until the malware has been completely obliterated.
Scan your device for malvertising-related threats
If you’ve noticed some strange activity on your Mac or have seen some apps on your system that you don’t remember downloading, don’t panic! Moonlock is here to help you in these situations.
Malvertising often delivers malware that hides deep within system files or browser settings, making manual cleanup nearly impossible. Moonlock has a Malware Scanner that will perform an extremely Deep Scan of your system, scanning hidden/dormant files and uncovering malicious files that don’t want to be found. Once the threats are found, it moves them immediately to Quarantine, where they can be reviewed and deleted.

Here’s how to check your Mac for malvertising-related malware:
- Download and open Moonlock.
- Find the Malware Scanner and run a Deep Scan.
- Moonlock will find everything that is hidden and dormant on your system.
- All of the threats that are found will be moved immediately to Quarantine.
- Once you review and look for clues on how the files go into your system, delete everything.
Sign up for a free trial of Moonlock to scan your Mac, remove hidden malvertising threats, and stay protected.

Change your browser settings back
Although Moonlock will remove malvertising-related threats and any other malware, it won’t automatically restore your browser settings. You can easily reset them yourself using the steps below.
Safari
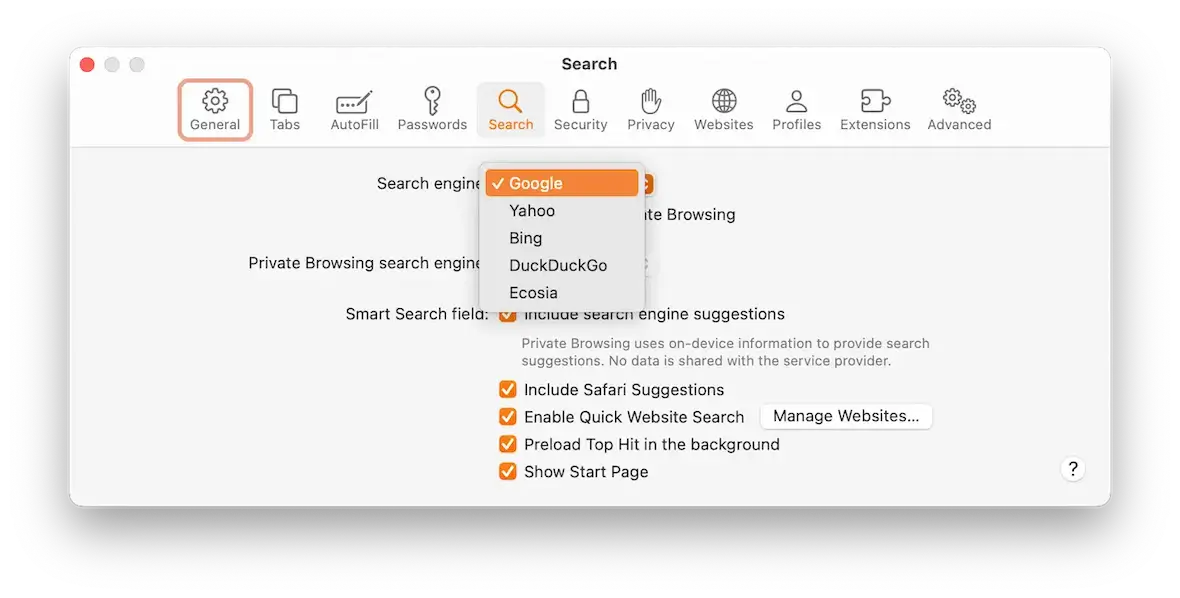
Go into your Safari settings and check the following:
- Safari > Settings > Extensions. Remove anything you didn’t install.
- Safari > Settings > General. Reset your homepage to what it was
- Safari > Settings > Search. Reset your default search settings back to your preferred search engine.
- Safari > Clear History… Delete all cache and temporary internet files to remove any possible malvertising traces.
Chrome
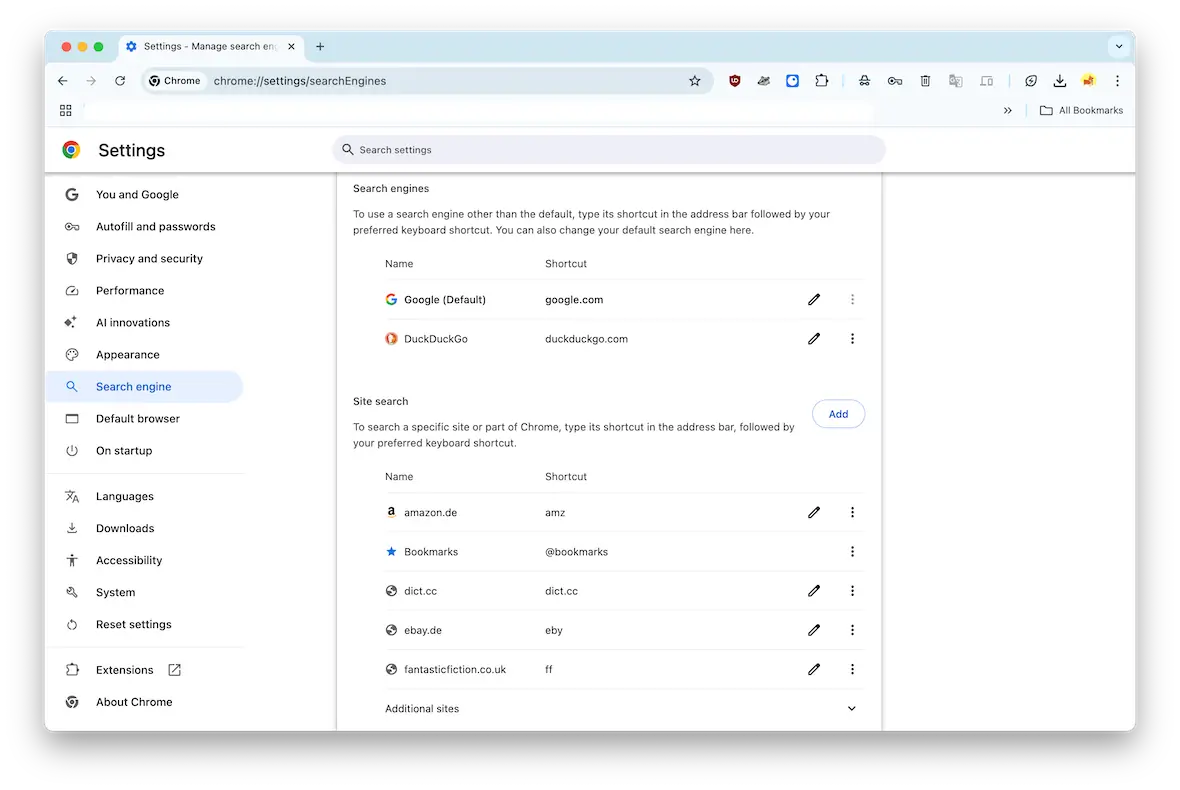
The process for changing settings back in Google Chrome is the same. Only the location differs:
- Settings > Extensions > Manage Extensions. Remove any unknown extensions.
- Settings > Appearance. Reset your homepage.
- Settings > Search Engine. Reset your default search settings.
- Settings > Privacy and Security. Delete all cache and temporary internet files.
Firefox
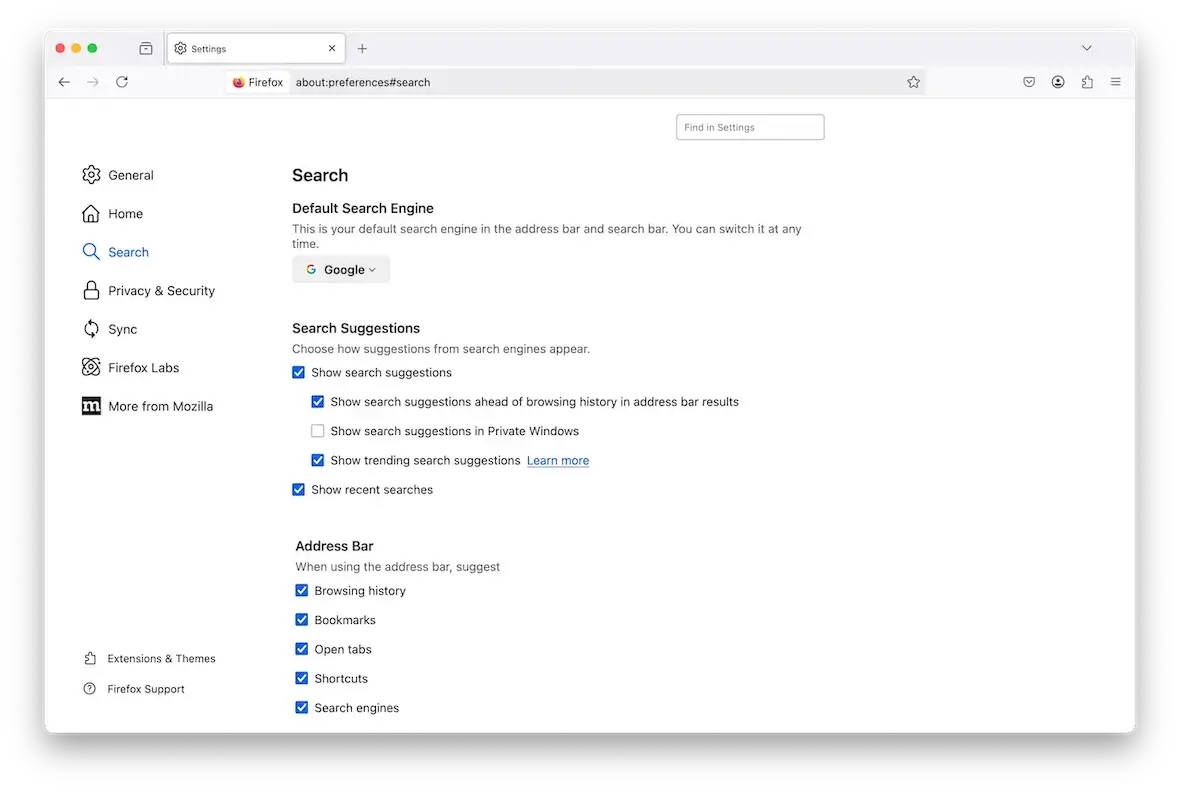
Finally, let’s cover Firefox. Again, it’s the same settings but different names for locations:
- Settings > Addons & Themes. Remove any unknown ones.
- Settings > Home. Reset your homepage.
- Settings > Search. Reset your default search settings.
- Settings > Privacy & Security. Delete all cache and temporary internet files.
Update everything
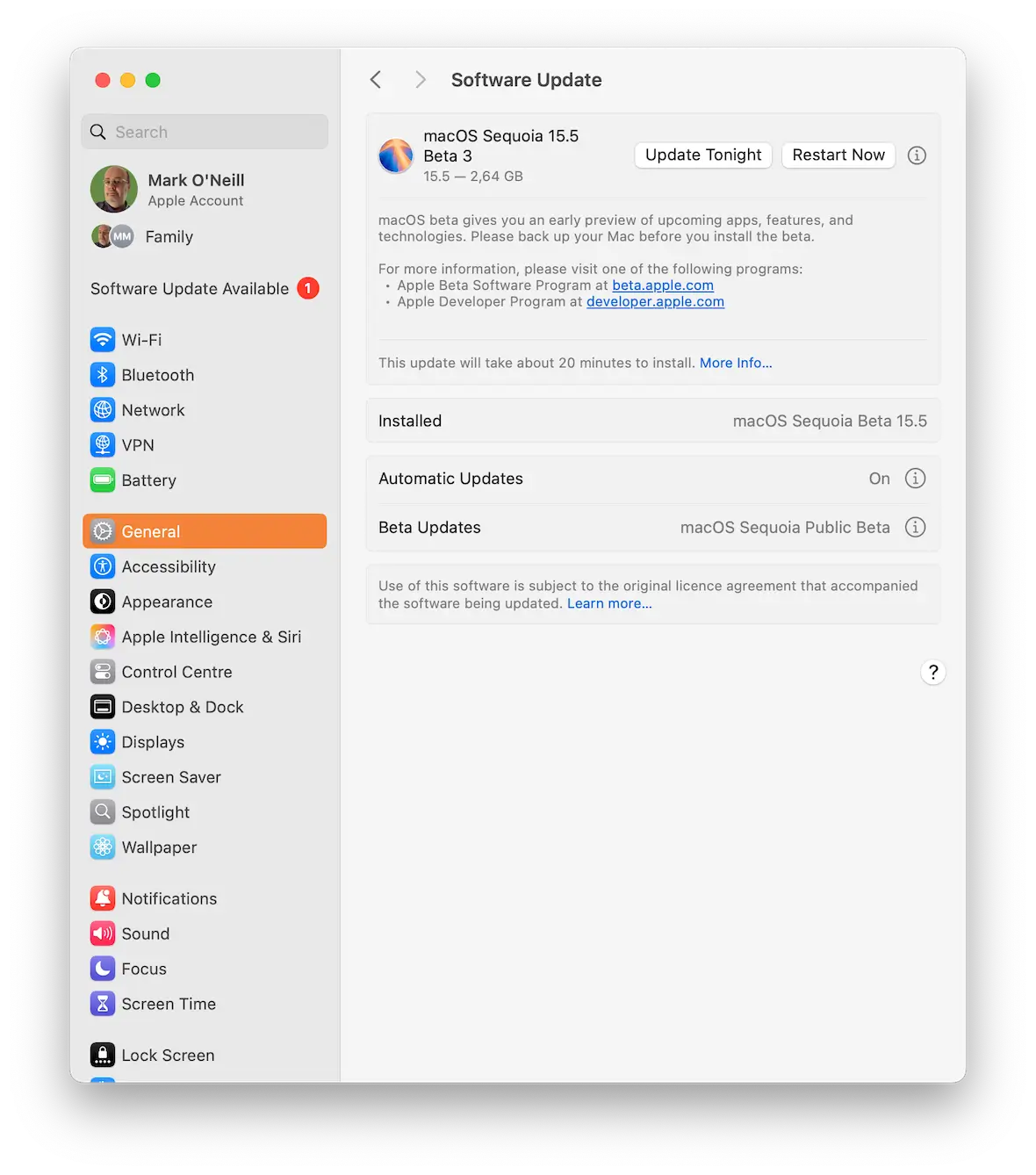
The next step is to make sure all apps and macOS are updated with the latest patches.
On your Mac, go to Settings > General > Software Update. Then go to your App Store and click your Apple account picture at the top-right. This takes you to your waiting app updates.
Delete any unknown or suspicious apps
Go to the Applications folder and see if there are any apps you didn’t install. Keep an eye out for gibberish names and/or blurry icons.
Delete any unknown apps in Login Items
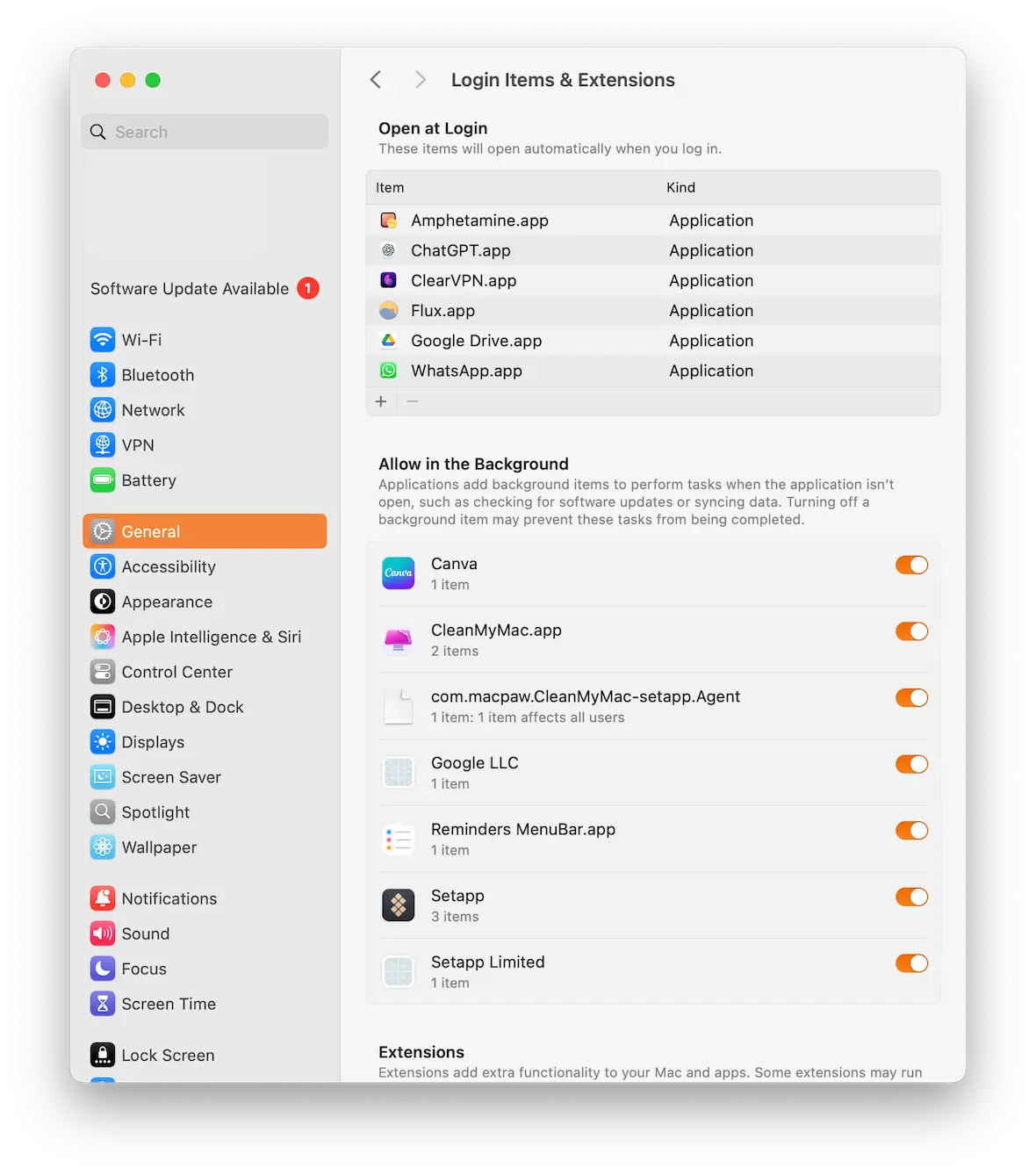
For obvious reasons, malware likes to automatically start up when the MacBook does. This is why your next port of call should be the Login Items section. You can find it by going to System Settings > General > Login Items & Extensions.
If you see any unfamiliar apps there, delete them and make sure the corresponding apps in the Applications folder are also gone.
Check for rogue configuration profiles
Configuration profiles are a valuable setting for malware to have. It gives them the necessary user permissions to do what they need to do.
Go to System Settings > Privacy & Security > Profiles. If you see any configuration profiles that you didn’t create, delete them immediately. This will likely require your administrator account details to remove.
Types of malvertising and real-world examples
This section will break down some malvertising examples and put a face on the menace by outlining some real-life malvertising events.
Malvertising types
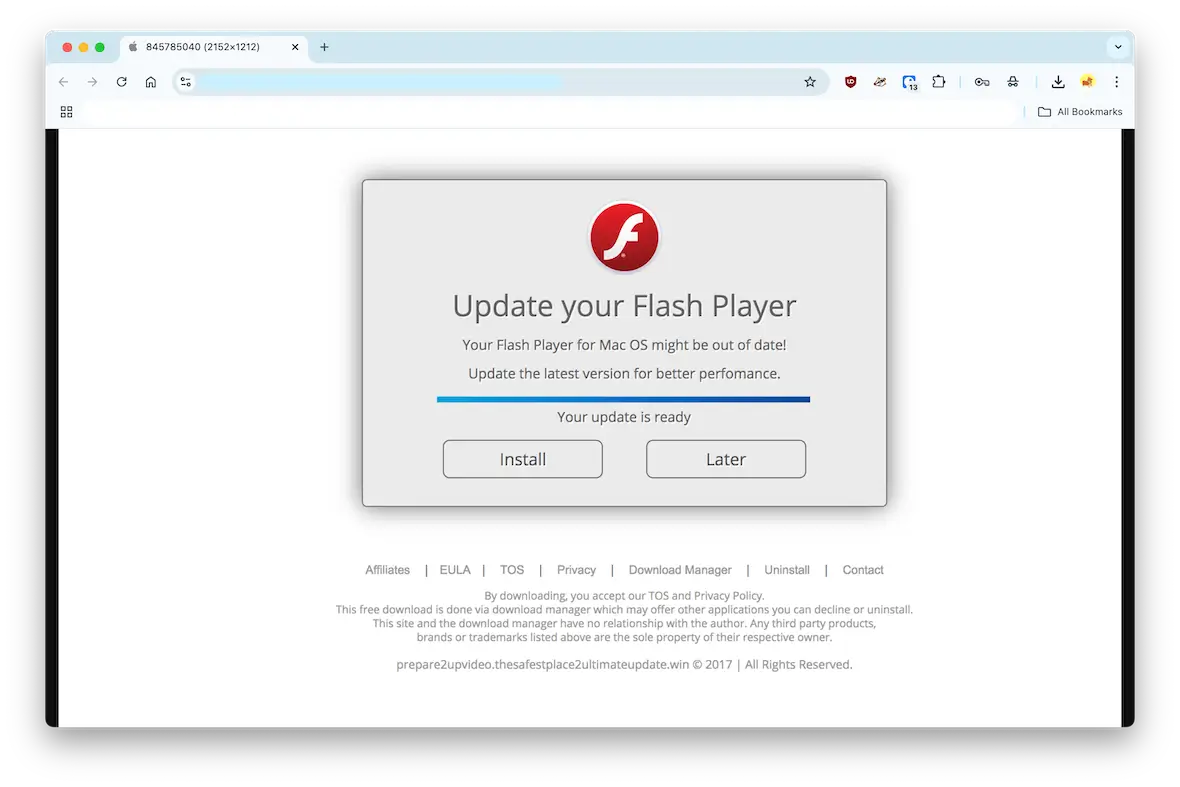
Here is how malvertising usually manifests itself to victims:
- Drive-by download ads: These are arguably the worst ones because you don’t even have to click them. Just visiting the website is enough for these ads to kick in in the background, looking for an outdated version of something on your device to exploit.
- Click-to-infect ads: Unlike drive-by ads, click-to-infect ads are exactly what the name describes. To get the malware, you would need to click the ad first. Ironically, these often warn you of virus infections.
- Redirect ads: Again, the name explains it all. When you click on this type of ad, you’re redirected to a malicious website where bad things await.
- Fake software update ads: Here comes our old nemesis again: Adobe Flash Player updates. But it can also appear as a browser update or an antivirus notification.
Real-world cases of malvertising
To illustrate how malvertising appears in the real world, check out these actual real-world cases.
The New York Times (2009)
Our first example is The New York Times, which accidentally hosted malvertising in 2009. The criminals posed as a legitimate advertiser to lower the media outlet’s guard, first sending them ads without any malware. Once these were approved, they switched to malware-infected ads.
Yahoo (2015)

Next up is Yahoo, which sent malvertising to millions of its users, who then got malware on their devices through that old favorite, Adobe Flash Player. The ads were placed on the main page, as well as the news section — in other words, the pages with the most traffic.
Spotify (2011 and 2024)
Spotify holds the very dubious distinction of being hit by malvertising twice. The first was in 2011 when the Spotify desktop app was redirecting users to different websites.
The second, in 2024, used playlists to send people to pirated software and spam. What was most notable about this one was that the criminals used SEO to make sure those playlists appeared high in search results.
Facebook (2024)
Not even Facebook has been spared from the curse of malvertising. In 2024, Facebook accounts were displaying malware-infected ads that sent victims to cloned versions of legitimate shopping brands. And, of course, the malware also stole browsing data just to rub salt into the wounds.
How to proactively avoid malvertising
By now, you might be convinced that there’s no escaping malvertising. However, there are still some things you can do to prevent malvertising and stop it in its tracks.
Use Moonlock
If you find yourself in a spot of trouble online, for instance accidentally downloading a suspicious file or opening a spam email with a suspicious attachment, you need Moonlock. Its Malware Scanner was designed specifically for Mac, to find and remove hidden threats from deceptive downloads, browser extensions, and background processes that often come with malvertising attacks.
Install an ad blocker
The next step is to install an ad blocker so you don’t see any ads at all. Some of the best ones are:
- Privacy Badger
- uBlock Origin (Chrome has indicated that they will stop supporting this one in 2025)
- Ghostery
However, ad blockers will break some websites. If this happens to you, ask yourself if you need to visit the site or not. The fact that the site needs ads in order to run properly is alarming in itself.
If you do need the site, you can disable the ad blocker for that site. Just remember to enable it again when you’re done.
Keep your operating system, browsers, and apps updated
Malware uses software and operating system vulnerabilities to jump onto target devices. Therefore, stay on top of all updates and install them as soon as they appear.
Recheck your system settings with Moonlock System Protection
Even if you think you have removed malvertising, you still need to double-check your security settings for your own peace of mind.
Moonlock’s System Protection will review your security settings, find any weak spots, and let you know how to patch these gaps. With step-by-step guidance, it will help you lock down your Mac from outsiders. Try Moonlock System Protection to make sure your Mac stays secure.
Despite all your precautions, you may still fall victim to malware. Fortunately, there are ways to mitigate the threat and greatly reduce the risk.Despite all your precautions, you may still fall victim to malware. Fortunately, there are ways to mitigate the threat and greatly reduce the risk.
This is an independent publication, and it has not been authorized, sponsored, or otherwise approved by Apple Inc. Mac, MacBook, and macOS are trademarks of Apple Inc.






