Apple defines Mac malware as “malicious software, which includes viruses, worms, trojan horses, and other programs that can harm your Mac or your privacy.” In simpler terms, malware is any type of software that is made with the specific intention of disrupting, damaging, or gaining unauthorized access to your computer.
Experts still do not agree on the exact quantity of Mac viruses that exist today. However, the answer can be more or less distilled and categorized into the following 10 types of computer viruses.
The 10 main types of computer malware to be aware of
As is the case with other devices, malware on a Mac can be installed when the user clicks malicious links or downloads compromised files from emails, messaging apps, or unsafe websites. These can come from phishing emails, fake software updates (such as the infamous Flash Player update pop-up), and even malware that installs itself without the target user’s consent or knowledge.
Some types of malware are merely annoying, while others can be used to launch devastating and catastrophic attacks. Those on the lower end of the spectrum could include browser hijackers, which are easier to remove when detected compared to more serious offenders like remote access trojans (RATs), ransomware, and keyloggers.
Some of the more dangerous types of malware can cause severe damage to a system, leading to financial losses and impacting a user’s life significantly. This is why you need to remove malware from a Mac right away.
Today’s malware doesn’t discriminate between operating systems, and the popular conception that Macs don’t get viruses or are immune to viruses is a seriously outdated idea. In fact, the increasing popularity of Macs has made the macOS ecosystem a much more attractive target for cybercriminals. The number of known viruses for Macs has, consequently, increased exponentially.
In general, all malware falls within 10 types:
- Viruses
- Worms
- Trojans
- Keyloggers
- Ransomware
- Spyware
- Adware
- Browser hijackers
- Rootkits
- Botnets
1. Viruses: The oldest type of malware
A virus is coded malware that usually breaches a computer as an executable or a word file program.
Once a virus executes, it will replicate and can modify codes, programs, and critical parts of the system. It can cause a computer to slow down, make it vulnerable, or even cause the system to collapse. And while viruses may be the oldest type of malware, they are still a relevant and severe threat.
For example, in 2021, the security firm Red Canary detected the Silver Sparrow virus. Silver Sparrow can breach Mac computers that run on Intel chips or the new M1 chip. Macworld says Silver Sparrow infected approximately 30,000 macOS systems in 153 countries. No one knows what this virus does, but it connects to a server once an hour. Security experts assure us it is a severe threat and could be gearing up for a powerful attack.
Viruses continue to evolve despite being the oldest tool in the arsenal of cybercriminals, and Mac users are no exception when it comes to virus attacks. Moonlock is the simplest way to detect and remove viruses on a Mac.
2. Worms: Malware that spreads through security vulnerabilities
Worms use computer networks to spread. Unlike viruses, which need a program to run, worms do not need a host. They can also link to other connected systems and spread beyond the device. Worms often prey on security vulnerabilities. Open source code and code sharing, very popular among modern developers, are perfect opportunities for worms to thrive.
In August 2020, a worm linked to projects posted on Github, where millions of developers host and share code, began spreading through Mac computers. The malware known as XCSSET can access data of Safari, login Apple details, Google, Paypal, Skype, Telegram, and others.
Cybercriminals use worms to steal data and credentials, inject code, and execute ransomware and crypto-jacking attacks. They can spread rapidly, and their shapeshifting capabilities make them very dangerous.
3. Trojans: Malware that unpacks other malware
Trojan horses, or simply “trojans,” gain access to a system and unpack different types of malware. They often present themselves as harmless, legitimate software and work in the background without the user knowing it. Worst of all, they can open backdoors for attackers to access devices.
For example, in 2021, a trojan called XcodeSpy spread through Xcode, a free application development environment created by Apple for developers to create apps that run on macOS, iOS, tvOS, and watchOS. Those who coded XcodeSpy used the code-sharing platform to create a trojan that, once installed on a Mac, opens backdoors and can download additional malware.
Sentinel Labs, the organization that discovered the trojan, says XcodeSpy can take screenshots, capture audio and video, upload and download files, and more.

4. Keyloggers: Malware that records what you type
The essence of a keylogger is straightforward. It is coded to register everything a person types. Cybercriminals use keyloggers to get passwords, credentials, financial information, and personal data.
Keyloggers rarely come alone in an attack. They are employed in conjunction with other malicious software. The 2014 Ventir Trojan, for example, gains access and unpacks a backdoor, spyware, and a keylogger. And while keyloggers are not as sophisticated as other malware, they still pose a serious risk to data theft and privacy, giving away every single strike of a keyboard to a cybercriminal.
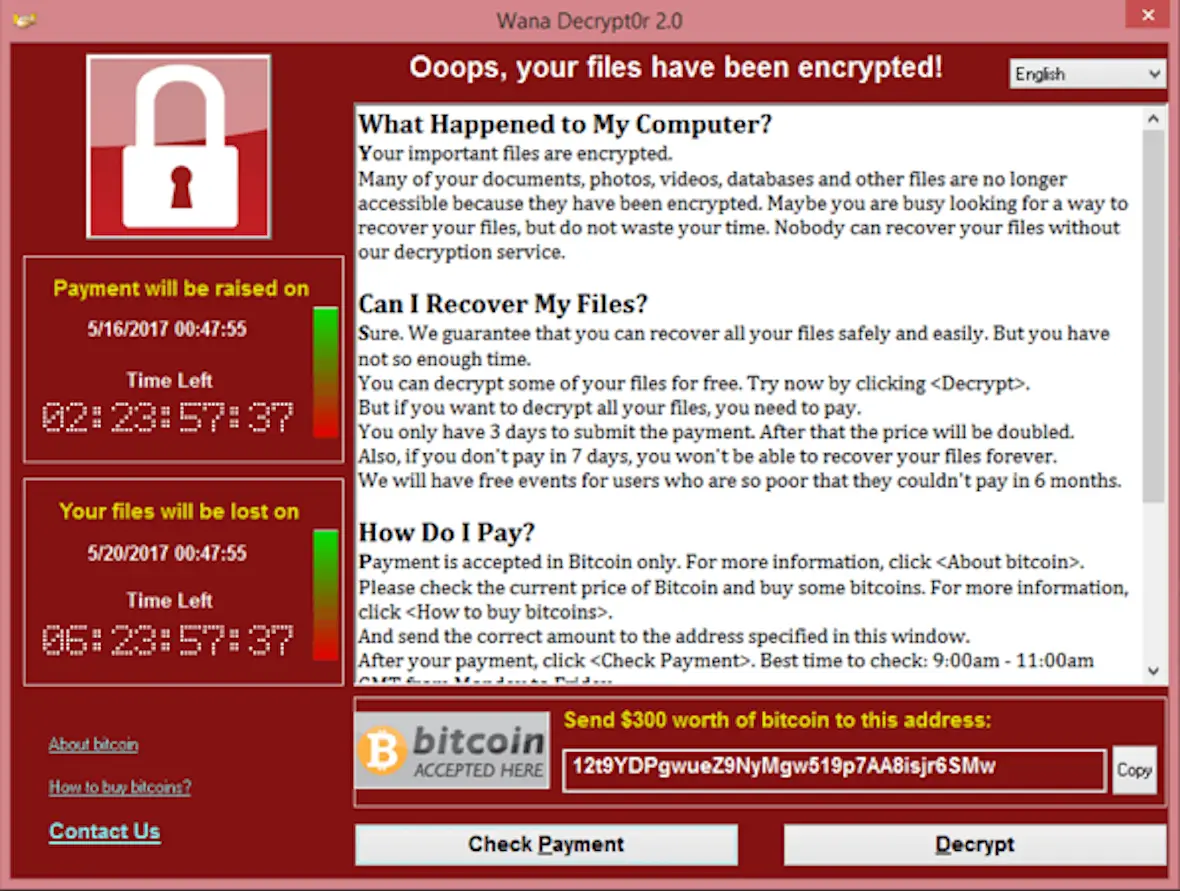
5. Ransomware: Viruses that demand a ransom
Ransomware is the fastest growing trend in cyber attacks. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) asserts that by 2021, there was one incident of ransomware every 11 seconds. Most ransomware attacks target small, medium, and large businesses.
In April 2021, the group Sodinokibi (REvil) executed a ransomware attack on Quanta, the Taiwan-based company that manufactures MacBooks. Attackers asked for $50 million in exchange for the encryption key. Quanta did not pay the ransom, and in retaliation, REvil leaked MacBook schematics and components.
6. Spyware: Eyes and ears on your device
Spyware is malware that installs in stealth mode on a device and spies on users. It can record audio, phone calls, text messages, screen activity, and video. Plus, it can access webcams and even install programs and change settings.
The most infamous modern spyware is Pegasus. Pegasus was developed by the Israeli cyber-arms company NSO Group and is used by governments to spy on citizens, activists, and journalists, violating fundamental human rights. And while Pegasus targets iPhone and Android devices, smartphones are often linked to personal computers, meaning your Mac might be vulnerable.
7. Adware: The nightmare of ads
Alongside viruses, adware is one of the oldest types of malware around. Adware will bombard users with irrelevant ads. This type of malware slows down a computer, can make it crash, and may eventually damage the system.
The main goal of an adware attack is to either disrupt a user by making it difficult for them to use their system or to reap money from the ads.
8. Browser hijackers: Viruses that take control of your browser
A browser hijacker, also known as a browser virus, is malware coded to take control of a browser. It can change browser settings and direct users to fake search engines or malicious pages. This type of malware is mostly just annoying and usually causes no immediate harm. However, users who are directed to malicious pages might download more dangerous malware.
Hackers tend to use legitimate or trusted sites to mount their attacks. Most browser hijackers use AkamaiHD.net. Akamai is not malware — it is a leading content delivery network used by companies like Facebook to stream audio and video and host downloads. But hackers use Akamai to control browsers and access browsing data.
Browser hijackers will slow down your Mac and occupy CPU and network bandwidth. They tend to breach computers through malicious pop-up warnings, bundling, and browser extensions.
9. Rootkits: Malware that steals admin privileges
Rootkit attacks are sophisticated and designed to give an attacker administrator root privileges. This kind of malware hides deep in the operating system. Often the only way of eliminating it is by reinstalling the OS.
Rootkits give attackers privileges to control every aspect of a device. They can be used as backdoors to download malware and launch ransomware or botnet attacks. Additionally, rootkit malware can go on the offensive when users attempt to remove it.
For example, the Thunderstrike malware, which appeared in 2015, installed a rootkit via Thunderbolt port using an infected host. Once installed, it could cause all sorts of damage, thanks to the administrator privileges the malware grants.
10. Botnets: Malware that infects multiple devices
Cybercriminals use the power of several computers to run botnet attacks, and each bot can infect another system. These are used for DDoS attacks, crypto-jacking, keylogging, and launching massive bulk malicious campaigns.
The first botnet attack to become world-famous was the Earth Link spammer, launched in 2000. The botnet sent over 1.25 million phishing email scams mimicking legitimate websites, Human Security explains. Another botnet attack in 2016, known as the Mirai botnet, left most of the east coast of the United States without internet access.
Examples of major malware attacks in recent years
To illustrate the severity of the problem, here are some real-world examples of major malware attacks within the past few years:
- SolarWinds (2020) – considered one of the most damaging supply chain attacks in history, this attack was made even worse by the fact that it took until the end of 2020 before it was discovered. The target was SolarWinds, a huge American IT company whose software is used by entities such as the United States government, Fortune 500 companies, private defense companies, and infrastructure operators. The attack has been attributed to Russia.
- Conti Ransomware (2020-2022) – described as a ruthless scheme by a cybercrime syndicate, this malware was active between 2020 and 2022. Again attributed to Russia, it strangely behaved like a corporation, with customer service support for negotiating ransoms. Its victims included US police departments, law firms, and manufacturers, asking for as much as 7 figures in ransom amounts.
- Kaseya VSA Ransomware (2021) – Again blamed on Russia, this ransomware attack targeted a remote management tool called Kaseya, used by thousands of companies all over the world, including schools, hospitals, and supermarkets. One supermarket had to close hundreds of their branches because the cash registers stopped working. The malware spread by posing as an innocent-looking security patch. Therefore, victims trusted it and installed it quickly. Ransoms ranged from tens of thousands of dollars up to several million dollars.
- HermeticWiper (2022) – Launched one day before the Russian invasion of Ukraine, HermeticWiper was a coordinated attack by Russia against Ukraine’s digital infrastructure in preparation for the next day’s attack. Its specific purpose was to wipe and cripple systems. This meant its targets were government buildings, infrastructure, and banks. However, the neighboring countries of Latvia and Lithuania were also affected. Due to the motive of the attack, this was classified as cyberwarfare.
- BlackCat Ransomware (2022–2024) – Notable for being the first malware written in the programming language Rust, BlackCat has been attributed to worldwide cybercrime syndicates. The fact it was written in Rust meant that it was more difficult to detect and remove. It made its way onto computers via compromised RDP or VPN logins and exploited vulnerabilities in business apps such as Microsoft Exchange.
Ways to defend against all types of malware
Here are the best ways to defend yourself against malware of all types. After all, forewarned is forearmed.
Use Moonlock
The best form of defense for malware attacks on a Mac is a tool that’s on the offensive 24/7. The recommended app is Moonlock. It’s free to try for 7 days, so go ahead and give it a shot!
Moonlock is a Mac-first cyber protection app with a powerful malware detection and removal tool. Simply fire it up and let it find and destroy all malware threats on your MacBook.
Update your devices regularly
Malware often enters machines through unpatched security vulnerabilities. So if you stay on top of installing patches, then you’re already seriously crippling a malware’s method of entry. As well as operating system updates, browser patches should also be quickly applied.
Don’t click links from unknown sources
Another favorite method of hackers is the infected weblink, which is spread via email, chat messages, SMS, QR codes, and email attachments. The rule of thumb is, if you don’t know the user, don’t click the link, no matter how tempted you might be. Don’t scan codes or open email attachments, either.
Back up all your files
If malware — such as ransomware — does strike, you need to mitigate the damage. Keeping a backup of all your files on a separate air-gapped drive will give you the option of completely wiping the system and reinstalling it from scratch.
Here are some more quick tips:
- Disable macros in Office files.
- Turn off autorun for USB drives.
- Remove any software that’s not being used.
- Use strong passwords on all your accounts.
- Train employees to recognize and report phishing emails.
- Use the lowest possible user privileges on computer folders and files.
- Encrypt as many files as possible to prevent them from falling into the hands of criminals.
- Install and enable a firewall.
- Use a VPN whenever possible.
While Mac security features may be the most impressive in the tech community, cybercriminals are getting more sophisticated in their attacks. Their toolbox is vast, and they are constantly creating new techniques to breach the Mac OS. Knowing what types of malware can affect your Mac and how they work is key to protecting your digital life.